Explain the Different Types of Security Policies
These policies decide the goals of the activities of the organization as a whole. This approach also allows you to apply customized security templates to each class of server.

Preventing Security Threats Computer Science Poster Cyber Security Awareness Cybersecurity Infographic Computer Security
EISP ISSP SysSP Posted on March 15 2017 by eastonanderson Enterprise Information Security Policy EISP directly supports the mission vision and directions of an organization.

. The Network Security policy may branch out into other policies depending on a companys infrastructure. Responsibilities rights and duties of personnel 11. Also known as the general security policy EISP sets the direction scope and tone for all security efforts.
However for the most part there are three broad types of IT security. Regulatory Information Security Policies While information security policies can be created by individual organizations many times they are enforced by law or as regulatory information security. These refer to the overall policies of the organization.
A system-specific policy covers security procedures for an information system or network. It will also ensure whether that person should be authenticated or not. This policy will establish and define standards procedures and restrictions for the disposition of non-leased IT equipment and media in a legal cost-effective manner.
By originated policy they refer to policy which originates from the top management itself. It is the strategic plan for implementing security in the organization. A regulatory policy sees to it that the company or organization strictly follows standards that are put up by specific industry regulations.
Security Incident Management Policy This policy defines the need for reporting and responding to incidents associated with the companys information systems and operations. Data support and operations 7. Information Security Policy Types.
Security policy types can be divided into three types based on the scope and purpose of the policy. This policy also includes other aspects like who will authorize the new devices that will be connected with network. It removes the unwanted sources of network traffic.
The master security policy can be thought of as a blueprint for the whole organizations security program. The following are the various types of policies. Level of data encryption is dependent on the algorithm used for encipherment.
Data backup policy 10. Security Document Hierarchy Information Security Policie s are high-level business rules that the organization agrees to follow that reduce risk and protect information. It is recommended that and organizations IT security legal and HR departments discuss what is included in this policy.
All of these policies should incorporate rules and behaviors when accessing the network. Security awareness and behavior 8. There are 2 types of security policies.
Additional policies may include Bluetooth baseline requirements policy router and switch security policy and wireless communication policy and standard. Technical security and administrative security policies. Three main types of policies exist.
Organizational or Master Policy. Access control standards Password complexity rules Password change policy User and. It is crucial to deeply understand these three different types of policies.
Network End-Point and Internet security the cybersecurity subcategory. 12 elements of an information security policy 1. The 5 Different Types Of Firewalls Deep Packet Inspection Work Advice Network Performance Cyber Security Tasc Management Cyber Security Security Security Technology Buttonup Infosec Cia Triad Triad Organization Help Infographic 8 Step Network Vulnerability Assessment Process Vulnerability Cyber Security Program Cyber Security Awareness.
Ad Award-winning cybersecurity documentation - editable policies standards and controls. Iv Externally imposed policy. Regulatory advisory and informative.
Intrusion Prevention policy This policy automatically detects and blocks the network attacks and browser attacks. Authority and access control policy 5. The Security Settings extension of the Local Group Policy Editor includes the following types of security policies.
Technical security policies describe the configuration of the technology for convenient use. There are three different types of security policies that are covered in the exam. Information security objectives 4.
The other various types of IT security can usually fall under the umbrella of these three types. Some subjects that might be covered in the ACP include. Network Policy This policy is to restrict the access of anyone towards the network resource and make clear who all will access the network.
In our model information security documents follow a hierarchy as shown in Figure 1 with information security policies sitting at the top. It is achieved by two famous techniques named Cryptography and Encipherment. Body security policies address however all persons should behave.
Koontz and ODonnell divide the sources of policy into the following four types. This mechanism is used to stop unattended access to data which you are sending. These policies are a master blueprint of the entire organizations security program.
All workers should conform to and sign each the policies. An example that is available for fair use can be found at SANS. 7 Key IT Security Policies Employee Awareness and Training Policy Password Management Policy Remote Access Policy Bring Your Own Device Policy Acceptable Use Policy Regular Backup Policy Disaster Recovery Policy 4 Best Practices for a Winning IT Security Policy Everything Must Have an Identity Access Control From End to End.
It also protects applications from vulnerabilities. It checks the contents of one or more data packages and detects malware which is coming through legal ways. Using OUs is the best method for separating specific security requirements for the different roles in your network.
The ACP defines what the employee will have access to. Functional Policies are prepared for different functions such as production marketing.
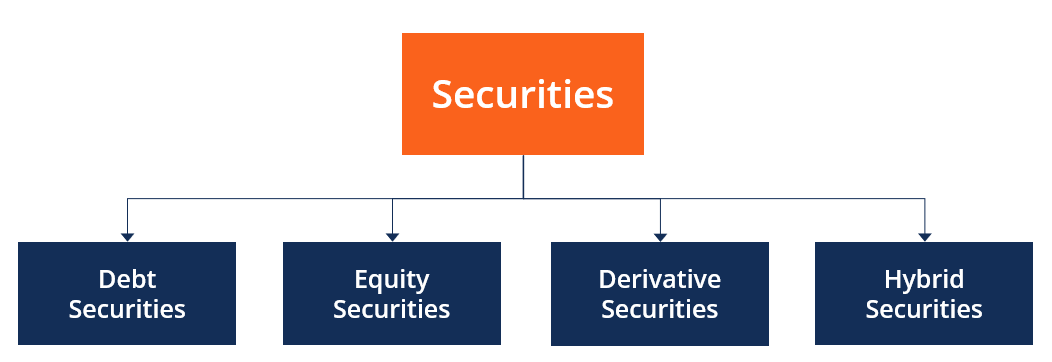
Types Of Security Overview Examples How They Work

Security Assessment Types Security Assessment Cyber Security Awareness Month Cyber Security Awareness

The 5 Different Types Of Firewalls Work Advice Network Performance Osi Model

Siconsult Five Perimeters To Define Enterprise Security Model Security Assessment Network Security Enterprise
Comments
Post a Comment